Configuring SMS OTP Authenticator
This document provides step by step instructions to set up SMS OTP configurations.
Configuring deployment.toml¶
-
Open
<IS_HOME>/repository/conf/deployment.tomlfile and configure the authenticator configurations as follows.[open_banking.sca.idp] name = "SMSAuthentication" -
Open
<IS_HOME>/repository/conf/common.auth.script.jsfile and update the configurations as follows.var psuChannel = 'Online Banking'; var onLoginRequest = function(context) { publishAuthData(context, "AuthenticationAttempted", { 'psuChannel': psuChannel }); executeStep(1, { onSuccess: function(context) { Log.info("Authentication Successful"); publishAuthData(context, "AuthenticationSuccessful", { 'psuChannel': psuChannel }); OTPFlow(context); }, onFail: function(context) { Log.info("Authentication Failed"); publishAuthData(context, "AuthenticationFailed", { 'psuChannel': psuChannel }); } }); }; var OTPFlow = function(context) { executeStep(2, { //OTP-authentication onSuccess: function(context) { context.selectedAcr = "urn:openbanking:psd2:sca"; publishAuthData(context, "AuthenticationSuccessful", { 'psuChannel': psuChannel }); }, onFail: function(context) { publishAuthData(context, "AuthenticationFailed", { 'psuChannel': psuChannel }); OTPFlow(context); } }); }; -
Run the following command in
<IS_HOME>/binand restart the server../wso2server.sh
Step 1: Adding SMS OTP Identity Provider¶
-
Sign in to the Management Console of WSO2 Identity Server at
https://<IS_HOST>:9446/carbon. -
Go to the Main menu > Identity > Identity Providers > Add.

-
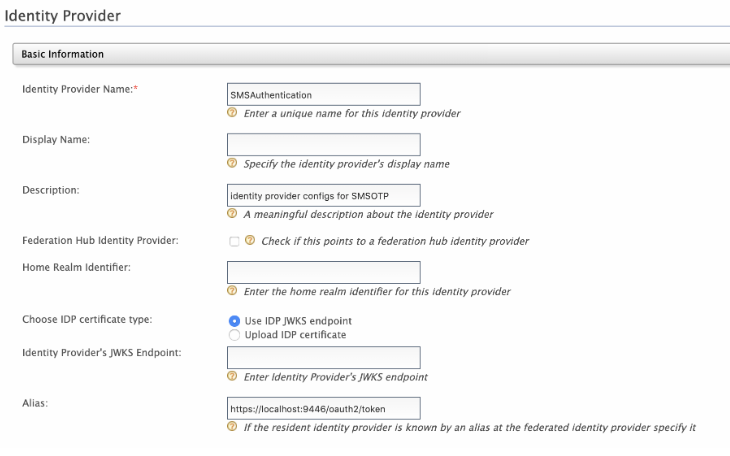
Fill the Basic Information section and name this identity provider as SMSAuthentication.
-
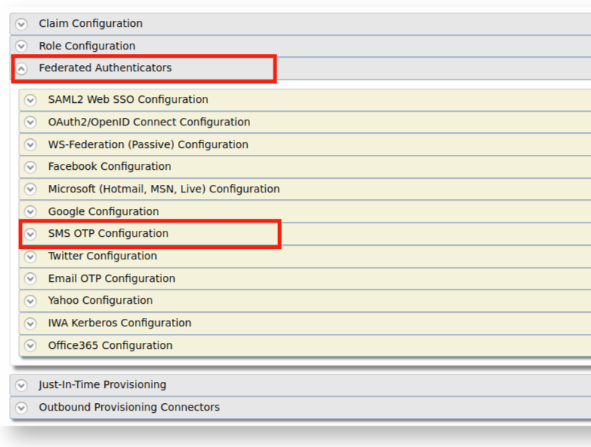
Expand the Federated Authenticators > SMS OTP Configuration section.
-
Select both the Enable and Default checkboxes. This is to enable and make the SMSAuthentication authenticator the default one.

-
Based on your SMS provider, fill out the SMS OTP configurations.
-
If Twilio is used as the SMS provider, go to https://www.twilio.com/try-twilio and create an account.
-
While registering the account, verify your mobile number and click on console home https://www.twilio.com/console to get free credits (Account SID and Auth Token).
-
Twilio uses a POST method with headers and the text message and phone number are sent as the payload.
-
-
Add the following sample configurations and click Register.
SMS URL : https://api.twilio.com/2010-04-01/Accounts/%7BAccountSID%7D/SMS/Messages.json HTTP Headers : Authorization: Basic base64{AccountSID:AuthToken} HTTP Payloads : Body=$ctx.msg&To=$ctx.num&From=urlencode{TrialNumber} HTTP Method : POSTSMS URL : https://api.twilio.com/2010-04-01/Accounts/AC34f40df03e20fb6498b3fcee256ebd3b/SMS/Messages.json HTTP Headers : Authorization: Basic QUMzNGY0MGRmMDNlMjBmYjY0OThiM2ZjZWUyNTZlYmQzYjo1ZmFkM2VkYzg4YWM1NTNiMmFiZjc4 NWI1MmM4MWFkYg== HTTP Payloads : Body=$ctx.msg&To=$ctx.num&From=+1 210-880-1806 HTTP Method : POST
Step 2: Configuring Account Lock¶
-
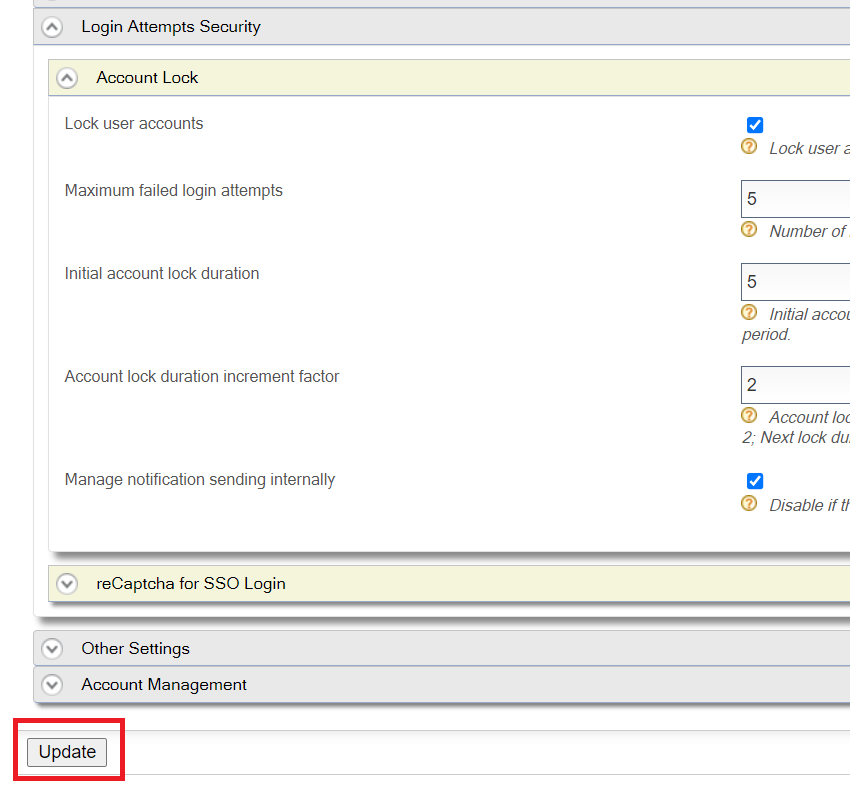
Go to the Main menu > Identity > Identity Providers > Resident > Login Attempt Security > Account Lock.


-
Select the Lock User Accounts checkbox.
-
Configure the Maximum Failed Login Attempts.
-
Scroll down and click Update.
Step 3: Configure mobile as a mandatory claim¶
-
On the Main menu > Identity > Claims > List.

-
Select
http://wso2.org/claimsfrom the list.
-
Locate Mobile from the list and select Edit.

-
Select Required and click Update.

More on Login Information...
In the authentication flow, if you log in as an admin user, it will prompt for the mobile number in the first attempt to log in. The Mobile number should be given in the format of the following example - 94714564567.
Note
Test scenarios can include attempting to log in using invalid usernames more than the allowed number of times, attempting invalid OTPs more than the allowed number of times, etc.